How to hide your IP address
How to hide your IP address
You have different options when it comes to hiding your IP address. Below are the most frequently used but that comes with feature additional security risks.
Using a Virtual Private Network (VPN)
Using a Virtual Private Network or a VPN is most reliable and convenient way available today for hide your real IP address. It is one of the most popular methods of maintaining your online privacy.

A VPN is a software service that encrypts all of the data sent to and from the internet and routes it through a VPN server in another location. In other words, the VPN creates an encrypted tunnel between you and the VPN service’s server.
Your computer or device connects to one of the VPN service’s servers located throughout the world and then uses its IP address rather than your own. This effectively hides your IP address so websites and online apps you visit only see the server’s IP address and not your own.
While an observer may be able to detect that you are connected to a VPN server, they will not be able to see the information passing through the tunnel since its encrypted
When you connect to a VPN server located in another country, your connection is assigned an IP address identifying it as being located in that country. This convinces Netflix, Hulu, gaming servers and other providers that you’re located in a licensed area, and they allow you to access the content.
Pros:
- Low acoustic noise and Easier to handle when cleaning stairs as not required to move heavy parts
- Your online privacy is maintained by hiding your real IP address
- Data is encrypted during transmission keeping it secure
- You may experience higher download speeds
- Ability to choose the country and city where you appear to be
- Can be used for torrenting or any online activity
- No logging of your online history
- Allowing access to Geo-Restricted contents
- Allows to use in multiple devices
Cons:
- The reliable VPN service require a small monthly subscription fee.
- Some VPNs companies may keep VPN logs of your activity.
- Some websites may refuse to connect if they suspect you are using a VPN.
Takeaway: VPNs are best and most widely used method to hide IP address, all your online traffic is encrypted so data transmission is secure.
Using a Proxy Server
Using a proxy server is similar in ways to a VPN but has some very important differences. A proxy server is a computer or an application that acts as a middleman (or a “proxy”) for requests your connected devices make to the internet.
It will allow you to stream or view websites that may be geo-blocked. After connecting to the proxy server, you are using its IP address to connect to websites.
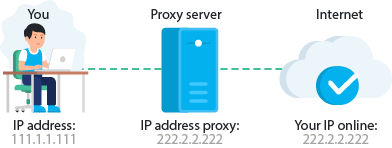
In the past, proxy servers were mainly used as a means of connecting multiple users to the internet in cases where a direct connection might not have been feasible. This was widely the case in the early, “dial-up” days of the internet.
In modern times, proxy servers are a way for a user to keep their identity and their original IP address undercover.
Your data is not encrypted and full address spoofing is not provided, so you can still potentially be monitored by your ISP or government.
While proxy servers work quite well and are, in many cases, less expensive than VPN services, they do not provide the encrypted connection protection a VPN does, leaving your activities open to prying eyes.
Pros:
- Can be used to get around geo-blocked contents.
- Hides your IP address at basic level
Cons:
- Slow data transmission speeds.
- The potential for using a compromised proxy server.
- Most proxy servers log your activity, so your activity can be monitored
- No data encryption
- Not legal in some countries
- Not compatible with mobile and tablets
Takeaway: Using a proxy server is potentially risk, you may consider managed proxy providers if you still wanted to use as they should have additional security.
Using the Tor Browser

The Tor browser is a software application that lets you use the Tor network to hide your IP and browse anonymously. It is a freeware, open-source program and can be run on many different operating systems.
The Tor Browser is free and sends your browser activity through a network of relays run by thousands of volunteers, which hides your actual IP address and make it difficult to impossible to track your online travels back to your IP address.
When you connect to Tor, your internet traffic is encrypted and routed through a random sequence of these volunteer “nodes,” which are sort of like proxy servers. Websites can only see the IP address of the last server in the sequence, called the exit node.
Each time you visit a website, the sequence of nodes changes. This makes it practically impossible to trace activity back to the original IP address.
While the Tor Browser is an efficient way to safely browse the internet, be advised that your browsing activities will be slowed down by quite a bit due to the extra leaps around the web that your browsing traffic is making.
Pros:
- Eliminates Internet censorship by unblocking all websites.
- Tor is an open-source software so there is reduced risk of vulnerability.
- Enables access to dark websites.
Cons:
- No encryption applied to your data.
- Can be monitored by higher authorities.
- Some websites block connections from known Tor nodes
- Tor is limited to amount of web traffic
- Slow performance due to using the onion network.
Takeaway: Since Tor uses a network of distributed relays, the performance of Tor Browser is much slower than the native browsers, not suitable for torrenting or streaming
Using a Public Wi-Fi Network

Alternatively, you may use public Wi-Fi services offered by a coffee shop, hotel or any public locations to connect your device, you will temporarily hide your usual IP address. Since you’ll be using their network’s IP address for as long as you’re online.
However, if you don’t use a VPN when you use an open public hotspot, you are opening yourself up to monitoring by any other user who is connected to that hotspot. In addition, that Wi-Fi hotspot is connected to the internet via an ISP, posing further monitoring issues.
Pros:
- Free access that can be found in many locations.
Cons:
- All traffic can be traced
- Unsecured network poses security risks to your machine and data.
- Unreliable connections due to the number of simultaneous connections.
Takeaway: We do not recommend using a public Wi-Fi hotspot to “hide” your real IP address. While using a public Wi-Fi hotspot offer you a slight amount of anonymity, but it poses valid security concerns.
Benefits of hiding your IP Address
You might wonder why I should care about hiding my IP address, but it comes with array of benefits. Hiding your IP address allows you to access blocked web sites, Hiding your geographical location, preventing Web tracking, avoiding a digital footprint, or to bypass any content filters, bans or blacklisting, stay anonymous online, work around the IP bans, access dark web, and protect your identity. There are several ways to hide your IP address, and each have advantages and disadvantages
By keeping it hidden not only will you obtain total online anonymity, but you’ll also get to experience true online freedom.
Why should I hide my IP Address
In the same way that there are issues with leaving your geolocation services online when you are moving about, there are issues with letting your IP address location information visible for every website you visit.
Primarily, there are issues about both personal and data security, as your geographic location can point out to other data about you.
Let’s take a look at some of the most common reasons why you want to hide your IP address,
To hide your physical location
Because most of us carry all of our personal data in our pocket everywhere, we go, personal cyber security and actual physical security overlap most of the time. If someone knows the IP geolocation of your smartphone, they know where the body holding that smartphone is.
Any malicious person who has constant access to this information can track your movements and know your schedule. While the hacker alone might not have any benefit to knowing this, they can sell the data collected to a wide range of criminals who will then know when you are not in your home.
Safeguarding your online privacy
As explained above, what is IP address and what kind of data it reveals, there is no place you can go online without someone watching. If you want to move around the Internet without being tracked by your ISP, ad networks, hackers or search engines, the only way is to hide the IP address. This way you can surf while maintaining your privacy.
Bypassing organizational online restrictions
Your workplace or school may restrict access to your favorite fantasy baseball site or your school blocking Netflix to keep your mind on your studies when you are using their network and IP address. If you can hide IP addresses you can get around these types of limitations.
Sometimes, your own government could even be blocking certain websites and services, whether out of a misguided desire to keep their citizens pure of heart or simply to keep them from information that would allow them to realize what’s really going on inside their own borders.
Protect your sensitive data
In the age of digital era, everything is connected. Even if you are not giving out your mobile IP address geolocation, your home devices will give an even worse type of information, your place of residence.
And it is a misconception that some serious hacking skills are needed to find you this way. You don’t need to hack into the mainframe and disable the algorithms to use an IP location lookup tool online and match it to the twelve numbers you have collected from your website.
This small breach could create a whole set of problems. From identity thieves using the data, they get to steal your identity and drain your bank accounts, or max your credit cards, to serious data collectors that will resell your info to much more sinister parties. Make sure to you have encrypted your most sensitive data when it resides in your PC or Mobile as well during data exchange over network
Even with all the governments, corporations, and all types of crime syndicates in the world, a much more pressing issue are the private photos of your child being sold to pedophiles over the unindexed pages of the dark web.
Evading government censorship
The easiest way to block someone from a platform or service is to block their IP address. Additionally, it is not illegal of a private company to ban anyone for whichever reason.
This may not have been an issue just a couple of years ago when most bans were for actual online harassment and dissemination of some truly obscene materials. But on today’s internet, you can be banned for a wide variety of reasons.
Politics, religion, sexuality, race, gender, or place of residence -all can be a basis for a permanent ban.
Additionally, if you are a publisher or a content creator of any sort, twitter mobs can be made and sent to your home, because you have left your real IP address online and they now have your IP address location.
Certain governments monitor and censor the online activities of their citizens. This data may be used against you in an attempt to prove anti-government sentiments and lead to criminal charges or worse. A way around this practice is to hide IP addresses whenever you go online.
Access to Geo-Restricted Contents
There are restrictions enforced in many geographic locations regarding the streaming or downloading services that you can access.
Content restrictions will be made on your IP address for a variety of reasons, this includes much more than just TV shows, with whole subjects being banned due to religious, political, or other reasons in many countries.
In some cases, this is due to the enforcement of copyright laws that are intended to prevent you from accessing a site that provides torrents with which to download media content.
If you are living in the European Union or the United States, these restrictions will usually be due to licenses and intellectual property rights. For instance, if you are living in the US and want to see the new season from a BBC show, you will need to change your IP address with a VPN to change your location, as it will be unavailable for a whole year in the States.
Hiding your IP address can get you around these blockades and allow you to access any site on the Internet.
Protection from hackers
Just as your ISP, search engines, and governments can follow you around by using your IP address, so can hackers. These evil entities may not just want to monitor your movements and may be able to learn your identity and location through the IP address. This opens you up to potential malware and other types of digital attacks.
If a hacker knows your IP address, they will know your location. With this info, they can make a VOIP call from your area to your local ISP representative and fool some bored customer service rep to give out your name and home address. It’s all downhill from there.
To Block DDoS Attacks
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. From a high level, a DDoS attack is like a traffic jam clogging up with highway, preventing regular traffic from arriving at its desired destination
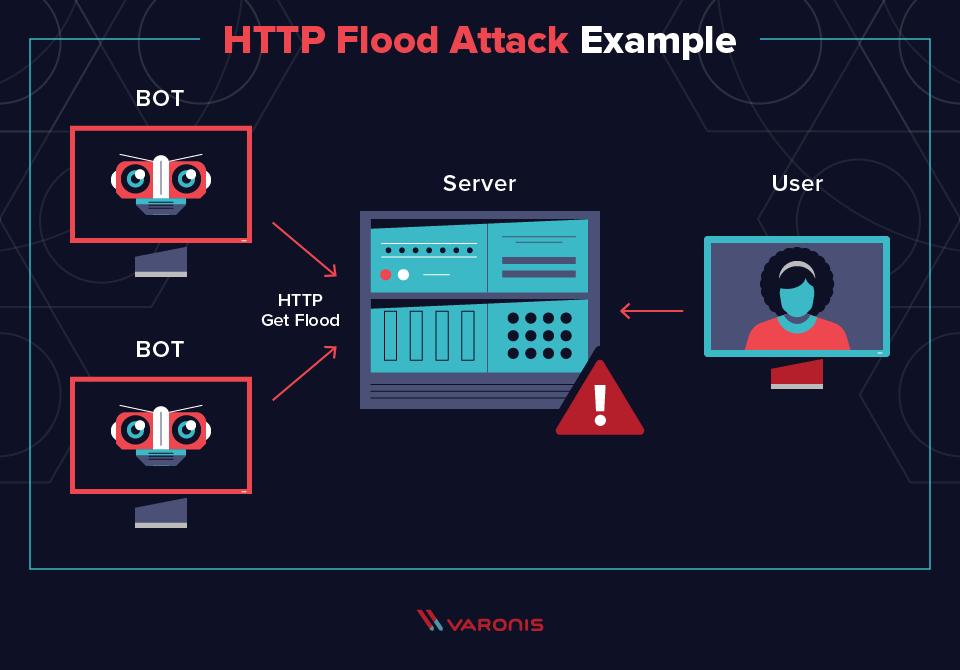
This DDoS attack technique has been used mostly to wage attacks on high-profile websites run by online merchants and banks. They will apply this method to cause the internet connection of the victim to slow to a crawl or shut down completely. The user is no longer be able to access websites, stream video, stay connected to gaming servers or perform any other online activity.
Using public WiFi safely
Free WiFi is everywhere these days and can be very attractive to users on the go or individuals who might not have their own WiFi network at home. While it sounds great, using free WiFi without hiding your IP address can be a recipe for disaster. Free and unsecured WiFi networks are notorious for enabling hackers to compromise the data of unsuspecting users. You don’t want them to see your real IP address and perhaps use it against you.